Foundational Cryptography Concepts for Cybersecurity: Real-World Applications in Networking
Foundational Cryptography Concepts for Cybersecurity: Real-World Guide


For those ready to launch or advance a career in IT, networking, or cybersecurity, understanding foundational cryptography concepts for cybersecurity is essential. This guide is designed for adults transitioning into tech, entry-level professionals moving forward, and anyone seeking practical, skills-based training for today’s cyber landscape. We’ll demystify key cryptographic principles, explain how they secure real-world networks, and show why these skills are critical for modern IT and security roles.
What Are the Foundational Cryptography Concepts for Cybersecurity?
Foundational cryptography concepts for cybersecurity refer to the essential methods and principles used to protect digital information—ensuring data remains confidential, authentic, and tamper-proof as it moves through networks or is stored on devices. These concepts underpin almost every secure transaction on the internet, from logging into your email to processing financial data, and are vital for anyone pursuing IT or cybersecurity careers.
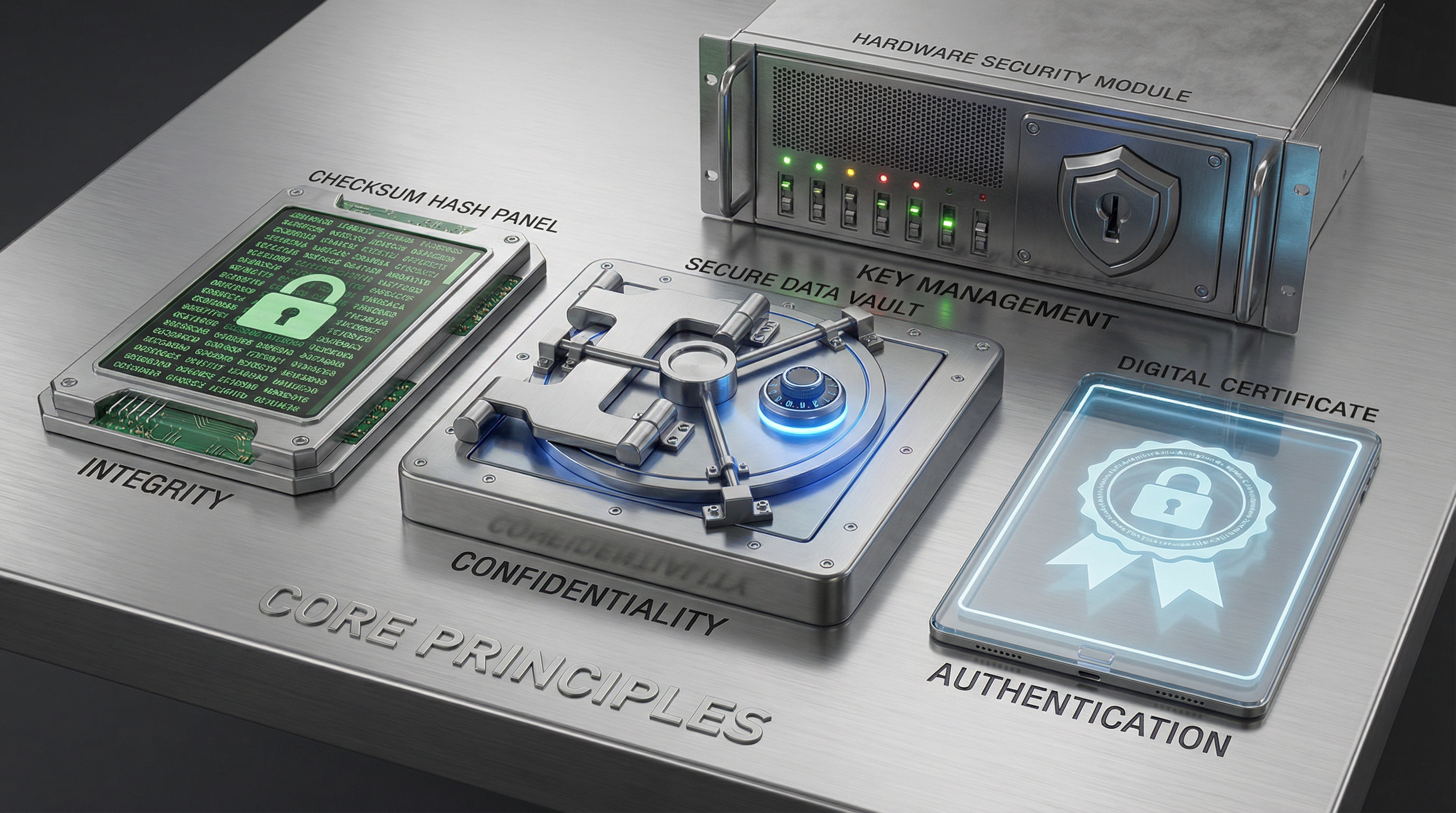
Core Principles of Cryptography in Cybersecurity
At the heart of cybersecurity is cryptography, the science of securing data through mathematical techniques. These core principles provide the backbone for defending sensitive information across digital networks and devices:
- Confidentiality: Only authorized parties can access the data, achieved through robust encryption.
- Integrity: Data cannot be altered without detection, using hash functions to ensure authenticity.
- Authentication: Confirms the identity of users or systems, leveraging digital signatures and certificates.
- Non-repudiation: Provides proof of actions, preventing denial of sending or receiving information.
- Key Management: Involves secure generation, storage, distribution, and rotation of cryptographic keys—a real-world operational challenge.
Types of Cryptographic Algorithms Used in Networking and Security
Symmetric-Key Cryptography
Symmetric encryption uses a single secret key for both encrypting and decrypting data. Algorithms like AES (Advanced Encryption Standard) and DES (Data Encryption Standard) are fast and suitable for bulk data, such as securing internal network traffic or storage devices. However, distributing the secret key securely across users or systems can be complex, making key management a vital skill.
Asymmetric-Key (Public-Key) Cryptography
With asymmetric cryptography, a public key encrypts data and a private key decrypts it. This system, powered by algorithms like RSA and ECC (Elliptic Curve Cryptography), enables secure communication between parties who have never met—critical for online transactions, secure web browsing (HTTPS), and digital signatures. Understanding public key infrastructure (PKI) and certificate authorities is crucial for IT professionals managing secure networks.
Cryptographic Hash Functions
Hash functions transform data into a unique, fixed-length string (the hash), which makes it easy to detect if information has been changed. Algorithms such as SHA-256, SHA-3, and Blake2/3 are widely used for password storage, file integrity verification, and digital signature schemes. No keys are required, but the uniqueness and security of the hash are essential for preventing attacks like hash collisions.
Hybrid Encryption
Many modern security protocols use hybrid encryption, combining the speed of symmetric algorithms for data transmission with the secure key exchange of asymmetric cryptography. This approach is standard in protocols like TLS (used in HTTPS) and SSH, balancing performance and security in enterprise environments.
How Are Cryptography Concepts Applied in Real-World Networking and IT?
Cryptography is not just theoretical—it is deeply embedded in daily IT and cybersecurity operations. Here’s how foundational cryptography concepts for cybersecurity translate into practical applications:
- Computer Password Security: Passwords are never stored in plaintext; instead, they are hashed and compared during login attempts, preventing exposure if databases are compromised.
- Digital Signatures: Used to verify the authenticity of documents, software, and transactions, ensuring information comes from a trusted source and has not been tampered with.
- Data Encryption at Rest and in Transit: Sensitive data in files, databases, and backups is encrypted to prevent unauthorized access. Encryption protocols like SSL/TLS and SSH secure data as it moves across networks.
- Securing Emails: Protocols like S/MIME and PGP use encryption and digital signatures to protect email content and attachments from interception or alteration.
- Authentication in Network Access: Multi-factor authentication, access tokens, and public-key certificates help confirm user and device identities, preventing unauthorized access.

Why Are Cryptography Skills Essential for IT and Cybersecurity Careers?
Organizations depend on cryptography to comply with regulations (such as GDPR, HIPAA, PCI DSS) and to prevent costly data breaches. For career changers and entry-level IT professionals, mastering foundational cryptography concepts for cybersecurity unlocks roles in network security, systems administration, security operations, and engineering. These skills are tested in certifications and are essential for hands-on tasks such as configuring firewalls, managing VPNs, and troubleshooting secure protocols.
Staying Ahead: Cryptography Trends and the Future in 2026
The field of cryptography is always evolving to counter new threats. Quantum computing, for example, is driving the development of post-quantum cryptography (PQC) algorithms that can withstand powerful future attacks. As organizations prepare for this transition, IT professionals will need to inventory existing cryptographic assets, implement new standards, and manage migration strategies. Ongoing learning and practical labs in real-world labs in cryptography are becoming even more valuable as the threat landscape shifts.
How Can You Build Hands-On Cryptography Skills?
To become proficient, focus on practical experience:
- Study Core Principles: Gain a strong grasp of confidentiality, integrity, authentication, non-repudiation, and key management through structured learning modules.
- Practice with Real-World Labs: Use sandbox environments to configure encryption, set up secure communications, and troubleshoot cryptographic protocols in simulated network environments.
- Work with Industry-Standard Tools: Familiarize yourself with encryption libraries, certificate management platforms, and secure communication tools widely used in the field.
- Understand Regulatory Requirements: Learn how cryptographic controls map to compliance frameworks like NIST CSF and ISO/IEC 27001.
- Stay Updated on Trends: Follow developments in post-quantum cryptography and emerging attacks to keep your knowledge current.
Our Network Engineer Program + Cybersecurity Accelerator at NGT Academy combines rigorous instruction, hands-on labs, and career coaching to help you master these essential skills and connect to real job opportunities in IT and cybersecurity.
Common Cryptographic Threats and How to Address Them
Even robust cryptography can fail if not implemented or managed correctly. Key risks include:
- Brute Force Attacks: Weak keys or passwords can be guessed by attackers; always use strong, complex keys.
- Man-in-the-Middle Attacks: Unsecured communication channels allow interception; enforce secure protocols like TLS and SSH.
- Hash Collisions: Weak or outdated hash algorithms (e.g., MD5, SHA-1) can be exploited; use modern alternatives like SHA-256 or SHA-3.
- Poor Key Management: Lost, stolen, or poorly protected keys render encryption useless; follow best practices for key lifecycle management.
- Expired or Misconfigured Certificates: Outdated certificates break trust chains and expose systems; implement regular audits and certificate renewal processes.
Getting Started with a Career in Cybersecurity and Networking
Whether you are transitioning from another industry or moving up from an entry-level IT role, cryptography is a core competency that will set you apart in the job market. Structured, skills-based training with tech career support, real-world labs and mentorship, like the programs at NGT Academy, provide the fastest path to career advancement. Our mission is to help one million people land tech jobs by 2030—learn more about how we support your journey.
FAQ
What are the main types of cryptography used in cybersecurity? Symmetric-key cryptography (e.g., AES), asymmetric-key cryptography (e.g., RSA, ECC), and hash functions (e.g., SHA-256) are the primary types. Hybrid encryption, combining symmetric and asymmetric methods, is also widely used.
How do cryptography skills help in a cybersecurity or networking job? They enable you to secure data, configure firewalls and VPNs, manage authentication systems, and ensure compliance with regulations, all of which are central to IT and security roles.
What is the role of key management in cryptography? Key management covers the secure generation, distribution, storage, rotation, and destruction of cryptographic keys, which is vital for maintaining effective security in any organization.
Why is post-quantum cryptography important for future-proofing IT careers? Quantum computers could break current public-key algorithms. Post-quantum cryptography prepares professionals and organizations to migrate to new, quantum-resistant standards, ensuring ongoing data protection.
Where can I get hands-on training in cryptography and cybersecurity? NGT Academy’s Network Engineer Program + Cybersecurity Accelerator offers practical labs, mentorship, and career coaching for real-world job readiness in IT and cybersecurity.
